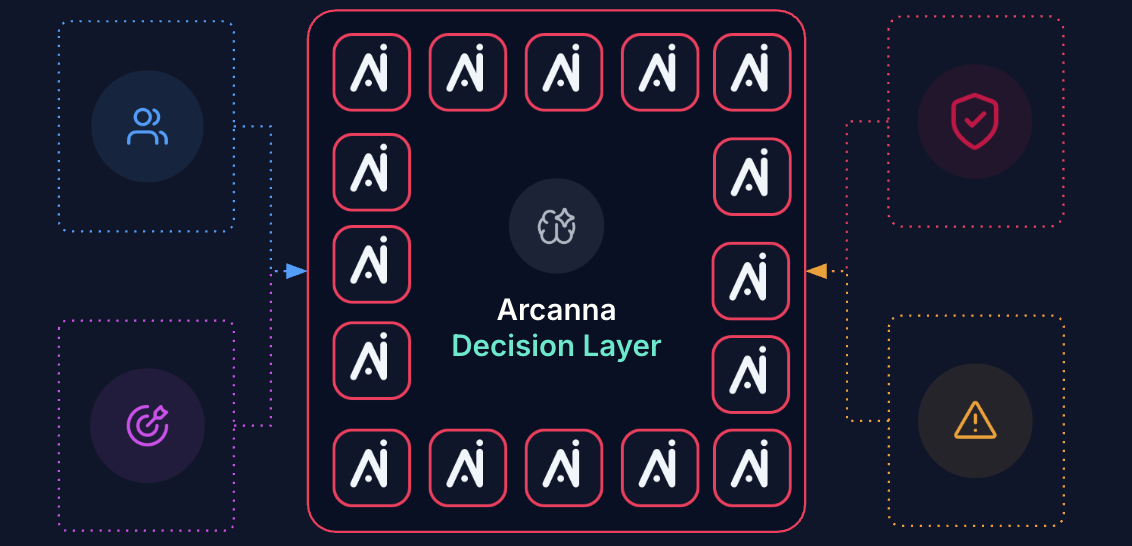
There is no doubt that AI in the SOC will be transformational. However, using the right kinds of AI in the right places is critical for building capabilities that can evolve and scale while also staying trustworthy.
Gartner names Arcanna.ai as a Cool Vendor for the Modern SOC.




.jpg)


.webp)


-3.webp)


.jpg)

.jpg)










.jpg)











.jpg)







